Posted by: Samker
« on: 01. October 2010., 17:20:30 »Zeus Trojan Bust Reveals Sophisticated 'Money Mules' Operation in U.S. also
Court documents released in connection with indictments announced on Thursday in a massive international cybercrime operation that resulted in millions of dollars being plundered from domestic bank accounts provide a fascinating -- if scary -- glimpse into how the crooks operated within the U.S.
The U.S Attorney's Office in Manhattan announced on Thursday that it had charged 37 individuals for their role in a scheme which involved the use of a sophisticated banking Trojan program and numerous "money mules" to steal from dozens of U.S. business accounts.
The charges in the U.S. followed similar arrests in the United Kingdom (post above), where authorities on Tuesday charged 11 Eastern European citizens in connection with the same scam. The operation in the U.S. was code-named ACHing Mules, in apparent reference to the fact that unauthorized automated clearing house (ACH) transactions were typically used to siphon money out of business accounts.
All of the individuals charged in the U.S. so far are from Russia and East European countries and were either money mules that helped transfer stolen money out of the U.S, or individuals who managed or recruited them.
Most of those charged on Thursday entered the country on J-1 non-immigrant visas, which are frequently used by students in cultural exchange programs and other short-term training programs. The visas allow those holding them to remain in the country for months at a time and permit them to open U.S. bank accounts.
A statement released by the Attorney's office said the actual thefts were perpetrated out of Eastern Europe by crooks who used the Zeus banking Trojan to break into computers at small businesses and small municipalities.
The malware was used to steal online banking credentials which were then used to access bank accounts belonging to the small business or municipality. The perpetrators would then withdraw money from the compromised accounts, typically in amounts just less than $10,000, and transfer it to fraudulent U.S. bank accounts set up by the money mules.
The mules would quickly withdraw the funds and send it to the perpetrators after retaining a portion of it -- about 10% -- for themselves.
One example is Ilya Karasev, a 22 year old Russian who has been charged with conspiracy to commit bank fraud, and two other charges. The conspiracy charge alone carries a maximum penalty of 30 years in prison.
Court documents describe Karasev as a mule who first entered the country on a J-1 Visa in May 2008 and then converted his status to a F-1 student Visa in December that year.
Karasev's misdeeds are alleged to have begun in April this year, when he opened a fraudulent bank account at TD Bank in New York using a fake Belgian passport issued under the fictitious name Fransoise Lewenstadd.
A few days later he opened another fraudulent bank account at another TD Bank branch this time using a Greek passport under the name of Alexis Harris. He opened a third account with the same bank a few months later this time using yet another foreign passport and the name Fortune Binot.
In addition to TD Bank, Karasev also opened several similar fraudulent accounts at Bank of America and JPMorgan Chase using his assumed identities. Over a matter of several months, the accounts were used to receive tens of thousands of dollars stolen from numerous small business accounts.
In each case Karasev would withdraw the bulk of the money almost as soon as it hit the fraudulent account using ATMs and over the counter transactions.
In some cases Karasev would make debit card purchases using the stolen funds. The court documents did not specify how Karasev would then transfer the money to the actual perpetrators in East Europe.
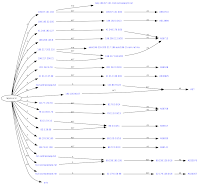
Karasev was one of over 24 individuals who belonged to an alleged money mule organization that was responsible for receiving funds stolen using the Zeus Trojan. The mules worked with computer hackers and individuals who could provide fake passports in helping them carry out their operations, according to court documents.
In many cases, the mules used three to four fake passports and identities to open multiple bank accounts, including two or three with the same bank.
One of the alleged ring leaders of the mule organization was Artem Tsygankov, a 22-year old Russia who like the others entered the U.S. on a J-1 visa. According to indictment papers, Tsygankov is alleged to have been responsible for recruiting numerous mules in the U.S.
Another individual, Sofia Dikova was described in court documents as the one in charge of obtaining the fake passports that were used in the scam. Dikova also acted as a mule occasion. Both Tsygankov, and Dikova face up to 30 years in prison if convicted on the consiparcy to commit fraud charges alone.
In addition to the charges by the U.S Attorney's office, Manhattan District Attorney Cyrus R. Vance, Jr., announced on Thursday the indictments of another 36 individuals for what was described as their participation in several large scale identity theft and cybercrime rings.
That group was allegedly responsible for stealing more than $860,000 from 34 corporate and individual accounts in the U.S., according to a statement from the District Attorney's office.
(PCW)
Court documents released in connection with indictments announced on Thursday in a massive international cybercrime operation that resulted in millions of dollars being plundered from domestic bank accounts provide a fascinating -- if scary -- glimpse into how the crooks operated within the U.S.
The U.S Attorney's Office in Manhattan announced on Thursday that it had charged 37 individuals for their role in a scheme which involved the use of a sophisticated banking Trojan program and numerous "money mules" to steal from dozens of U.S. business accounts.
The charges in the U.S. followed similar arrests in the United Kingdom (post above), where authorities on Tuesday charged 11 Eastern European citizens in connection with the same scam. The operation in the U.S. was code-named ACHing Mules, in apparent reference to the fact that unauthorized automated clearing house (ACH) transactions were typically used to siphon money out of business accounts.
All of the individuals charged in the U.S. so far are from Russia and East European countries and were either money mules that helped transfer stolen money out of the U.S, or individuals who managed or recruited them.
Most of those charged on Thursday entered the country on J-1 non-immigrant visas, which are frequently used by students in cultural exchange programs and other short-term training programs. The visas allow those holding them to remain in the country for months at a time and permit them to open U.S. bank accounts.
A statement released by the Attorney's office said the actual thefts were perpetrated out of Eastern Europe by crooks who used the Zeus banking Trojan to break into computers at small businesses and small municipalities.
The malware was used to steal online banking credentials which were then used to access bank accounts belonging to the small business or municipality. The perpetrators would then withdraw money from the compromised accounts, typically in amounts just less than $10,000, and transfer it to fraudulent U.S. bank accounts set up by the money mules.
The mules would quickly withdraw the funds and send it to the perpetrators after retaining a portion of it -- about 10% -- for themselves.
One example is Ilya Karasev, a 22 year old Russian who has been charged with conspiracy to commit bank fraud, and two other charges. The conspiracy charge alone carries a maximum penalty of 30 years in prison.
Court documents describe Karasev as a mule who first entered the country on a J-1 Visa in May 2008 and then converted his status to a F-1 student Visa in December that year.
Karasev's misdeeds are alleged to have begun in April this year, when he opened a fraudulent bank account at TD Bank in New York using a fake Belgian passport issued under the fictitious name Fransoise Lewenstadd.
A few days later he opened another fraudulent bank account at another TD Bank branch this time using a Greek passport under the name of Alexis Harris. He opened a third account with the same bank a few months later this time using yet another foreign passport and the name Fortune Binot.
In addition to TD Bank, Karasev also opened several similar fraudulent accounts at Bank of America and JPMorgan Chase using his assumed identities. Over a matter of several months, the accounts were used to receive tens of thousands of dollars stolen from numerous small business accounts.
In each case Karasev would withdraw the bulk of the money almost as soon as it hit the fraudulent account using ATMs and over the counter transactions.
In some cases Karasev would make debit card purchases using the stolen funds. The court documents did not specify how Karasev would then transfer the money to the actual perpetrators in East Europe.
Karasev was one of over 24 individuals who belonged to an alleged money mule organization that was responsible for receiving funds stolen using the Zeus Trojan. The mules worked with computer hackers and individuals who could provide fake passports in helping them carry out their operations, according to court documents.
In many cases, the mules used three to four fake passports and identities to open multiple bank accounts, including two or three with the same bank.
One of the alleged ring leaders of the mule organization was Artem Tsygankov, a 22-year old Russia who like the others entered the U.S. on a J-1 visa. According to indictment papers, Tsygankov is alleged to have been responsible for recruiting numerous mules in the U.S.
Another individual, Sofia Dikova was described in court documents as the one in charge of obtaining the fake passports that were used in the scam. Dikova also acted as a mule occasion. Both Tsygankov, and Dikova face up to 30 years in prison if convicted on the consiparcy to commit fraud charges alone.
In addition to the charges by the U.S Attorney's office, Manhattan District Attorney Cyrus R. Vance, Jr., announced on Thursday the indictments of another 36 individuals for what was described as their participation in several large scale identity theft and cybercrime rings.
That group was allegedly responsible for stealing more than $860,000 from 34 corporate and individual accounts in the U.S., according to a statement from the District Attorney's office.
(PCW)




 Total Members: 14197
Total Members: 14197