The bounceback e-mail messages come in at a trickle, maybe one or two every hour. The subject lines are disquieting: "Cyails, Vygara nad Levytar," "UNSOLICITED BULK EMAIL, apparently from you."
You eye your computer screen; you're nervous. What's going on ? Have you been hacked? Are you some kind of zombie botnet spammer?
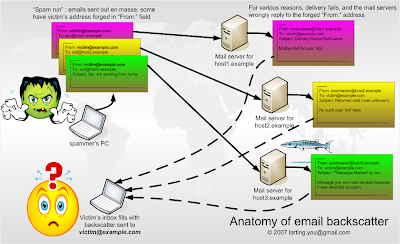
Nope, you're just getting a little backscatter -- bounceback messages from legitimate e-mail servers that have been fooled by the spammers.
Spammers like to put fake information in their e-mail messages in order to sneak them past e-mail filters. Because e-mail filters now just delete messages that come from nonexistent domains, the spammers like to make their messages look like they come from real e-mail addresses. That means, if your e-mail address has been published on the Web somewhere, you're a prime candidate for backscattering.
The spammer finds your address, or sometimes even guesses it, and then puts it in the "from" line of his messages, sending them out to hundreds of thousands of recipients. When the spam gets sent to an address that is no longer active, it can sometimes be bounced back ... to you.
Although Sophos estimates that backscatter makes up just two percent or three percent of all spam, antispam vendors say these messages are on the rise lately.
Users often think that the backscatter may be a sign that their computer has been hacked and is sending out spam messages, said Brad Bartman, a global support manager with Text 100, a public relations consultancy. "They look at it and they're like, 'Whoa, is my PC infected with a virus?'" he said.
Backscatter rarely hits more than one or two employees at the same time, so it isn't particularly disruptive. But it does worry users, he said. "It's mostly a psychological thing."
With their e-mail addresses widely circulated on press releases, Text 100's PR specialists are the ideal candidates for backscatter.
Because backscatter comes from legitimate mail servers, it can cause special problems. In fact, some security researchers believe that the spammers have been intentionally sending messages that will be bounced back as a way to sneak around spam filters. That's because some mail servers bounce back the original message as part of their notice.
Dan Wallach, like Text 100's Bartman, was hit with a flood of backscatter messages earlier this week. Wallach, an associate professor with Rice University's Department of Computer Science, said that many of the messages he received contained links to suspicious executable files hosted on different Web sites.
"I'll bet that some spammer is rationally thinking 'error messages! Maybe I can get my message through via error messages!'" Wallach said in an e-mail interview. "They don't need many responses before this sort of tactic could be considered to be a success."
At its worst the phenomenon can even wipe Internet servers off the map.
Last month, Stephen Gielda, president of Packetderm, upset a fraudster who was trying to use his anonymous Internet service. Soon his servers were inundated with a tidal wave of backscatter messages. At one point, he was being hit by 10,000 bounceback messages per second, enough to throttle the server's Internet connection.
Gielda had to take his site off-line for five days as he waited for the problem to abate. "I'm used to backscatter, but I'd never seen it at this level before," he said.
While backscatter is extremely hard to filter out, it is a problem that can be fixed.
Backscatter comes in three varieties: messages from mail servers, saying that there is no such user available; "out of office" automated reply messages; and so-called challenge-response messages, which tell the sender that his message will be delivered only once he responds to the bounceback and confirms that the e-mail is coming from a legitimate address.
Security experts say that people should simply stop using these last two types of bounceback messages.
As for "no such user" bouncebacks, that can be fixed too. There are a few e-mail standards that could help with the problem: Variable Envelope Return Path(VERP) and Bounce Address Tag Validation (BATV), for example.
But the problem would largely disappear if server administrators configured their mail servers to immediately reject mail that is sent to nonexistent users, rather than accepting it and then bouncing it back to the faked addresses. Some ISPs (Internet service providers), AOL for example, have done this and have largely eliminated their role in the problem.
If there is spam in the backscatter message, antispam software should filter it out, but if a message has an ambiguous subject line, like "Hey" and the spam message stripped out, the backscatter will look like a legitimate bounceback and is probably going to get through, said Dmitry Samosseiko, manager of Sophos Labs Canada.
"This is a serious problem that is hard to deal with, to be honest," he said. "We can blame spammers for causing the issue in the first place, but it exists because of the mail servers that are not configured to deal with spam."
(Copyright by PC World)
 Total Members: 14197
Total Members: 14197 Latest: Levine
Latest: Levine Total Posts: 43431
Total Posts: 43431 Total Topics: 16526
Total Topics: 16526 Online today: 2965
Online today: 2965 Online ever: 51419
Online ever: 51419 Total Members: 14197
Total Members: 14197 Latest: Levine
Latest: Levine Total Posts: 43431
Total Posts: 43431 Total Topics: 16526
Total Topics: 16526 Online today: 2965
Online today: 2965 Online ever: 51419
Online ever: 51419