Popular WordPress Plugin Comes with a Backdoor, Steals Site Admin CredentialsCustom Content Type Manager WP plugin contains a backdoorSecurity researchers have unmasked the wicked actions of a WordPress plugin that was installing a backdoor through which it was altering core WordPress files so it could log and steal user credentials from infected sites.First signs of something being wrong were spotted by the Sucuri team, a company that provides website security. Sucuri's researchers were alerted by one of their clients to the presence of a weirdly named file (auto-update.php) that didn't exist until a recent plugin update.
The plugin in question was
Custom Content Type Manager (CCTM), a popular WordPress plugin for creating custom post types that, in the three years since it was uploaded on the WordPress plugin repo, has amassed quite a following, being currently installed on more than 10,000 sites.
Custom Content Type Manager version 0.9.8.8 contains malicious codeAs
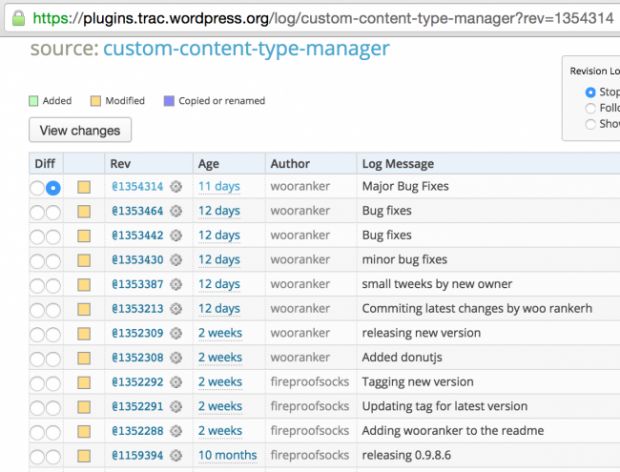
Sucuri's investigation revealed, in the past two weeks, the plugin that looked like an abandoned project for the last 10 months, mysteriously changed owner, and immediately after, the new developer, named wooranker, updated the plugin and pushed out a new version.
All the changes he made to the plugin were of a nefarious nature. First, there was the addition of the auto-update.php file, which included the ability to download files from a remote server on the infected website.
Additionally, wooranker also added the CCTM_Communicator.php file, which worked together with another, older, legitimate plugin file. The purpose of these two files was to ping wooranker's server about the presence of a newly infected site.
Besides gathering info on the victim's site, this plugin also tapped into the WordPress login process and recorded usernames and the password, albeit in encrypted format, sending the data to the wordpresscore.com server.
Some users were auto-updated to this malicious plugin versionThese two modifications were pushed out as Custom Content Type Manager version 0.9.8.8, which in many cases the users themselves installed or were automatically installed on their sites if the auto-update feature was turned on.
Once wooranker gathered data about infected sites, Sucuri says he tried to access his victims. In the case they analyzed, Sucuri saw that the hacker attempted to log in manually on one of the infected sites but didn't manage to authenticate because that site's owner had changed the login URL to a custom link.
Seeing his login attempts thwarted, wooranker quickly changed tactics, and Sucuri says he used the auto-update.php backdoor and forced the target's site to download and install another file called c.php, which would create another file, more exactly, wp-options.php (WordPress uses wp-settings.php).
This latter file had only one purpose, and that was to alter core WordPress files. The files it edited were wp-login.php, wp-admin/user-new.php, and wp-admin/user-edit.php.
Hacker found a way to record and steal passwords in cleartextThe hacker's alterations made sure that he was able to control user login, creation and edit commands, intercepting user data before being encrypted, and sending the user's cleartext passwords to wooranker's server.
Furthermore, wp-options.php also created an admin account on the infected website, with the credentials support / support@wordpresscore.com, which he could use if anything else failed.
All of this meant that wooranker would always have an admin account on all infected websites, and he would always be notified of what passwords users were using when accessing infected sites.
Did the hacker reveal his true identity?And just in case the CCTM_Communicator.php file had problems reporting on infected websites, wooranker also included his own set of JavaScript analytics code, loaded via the CCTM plugin as a fake jQuery version.
This JavaScript file was reporting all new infections to the donutjs.com domain. In fact, all the domains Sucuri discovered used in this attack were linked and registered under the name of Vishnudath Mangilipudi, a developer from Andhra Pradesh, India.
Sucuri didn't accuse Mangilipudi of being the hacker, since he could have easily had his identity stolen, just like the rest of us. As for wooranker, the same developer is also an admin on the
Postie WordPress plugin. Sucuri says that Postie is still managed by its original author, and that there's no malicious code inside it.
WordPress admins who have this plugin installed should remove it right away, roll back the core WordPress files to their standard versions, and if they really have to keep the CCTM plugin on their sites, use the last stable version, which is considered 0.9.8.6 (0.9.8.7 has a security flaw).
Sucuri wasn't the first to identify the plugin's behavior, with some users on the WordPress forums
having reported CCTM three days ago, but to be fair, they didn't actually see the auto-update.php file as a backdoor, but as a vulnerability that needed to be fixed.
 Original article: http://news.softpedia.com/news/popular-wordpress-plugin-comes-with-a-backdoor-steals-site-admin-credentials-501383.shtml
Original article: http://news.softpedia.com/news/popular-wordpress-plugin-comes-with-a-backdoor-steals-site-admin-credentials-501383.shtml
 Total Members: 14197
Total Members: 14197 Latest: Levine
Latest: Levine Total Posts: 43441
Total Posts: 43441 Total Topics: 16533
Total Topics: 16533 Online today: 3223
Online today: 3223 Online ever: 51419
Online ever: 51419 Total Members: 14197
Total Members: 14197 Latest: Levine
Latest: Levine Total Posts: 43441
Total Posts: 43441 Total Topics: 16533
Total Topics: 16533 Online today: 3223
Online today: 3223 Online ever: 51419
Online ever: 51419