The Conficker worm today has begun to phone home for instructions but has done little else. Conficker was programmed to today begin actively visiting 500 out of 50,000 randomly generated web addresses to receive new instructions on how to behave. Conficker has begun to do this, according to security company F-Secure, but so far no doomsday scenarios have emerged.

Among security experts, the consensus seems to be that very little will happen today. This may be in part because of the high amount of publicity Conficker has received, but then again April 1 is not the first time Conficker has been programmed to change the way it operates. Similar trigger dates have already passed with little change, including January 1, according to according to Phil Porras, a program director with SRI International. Security experts at Symantec, the maker of Norton Antivirus, also believe the threat is overblown and says Conficker today will "start taking more steps to protect itself" and "use a communications system that is more difficult for security researchers to interrupt."
Technology companies and experts across the globe have been working together to halt the spread of Conficker, disrupt its communications and uncover who created the worm. Microsoft has even issued a $250,000 bounty for information leading to the arrest and conviction of Conficker's authors. Despite the security sector's best efforts, very little is known about the origins of Conficker or its purpose. Nevertheless, some breakthroughs have been achieved. On March 30, Security experts with the Honeynet Project discovered a flaw in Conficker that makes it much easier to detect infection. IBM researcher Mark Yayson also believes he has discovered a way to "detect and interrupt the program's activities," according to The New York Times.
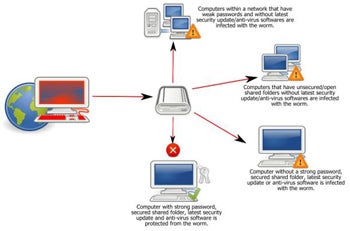
Since the Conficker worm was discovered in October 2008, the malware has only received programming updates from its author and worked to infect other computers. Conficker is believed to have infected 10 million computers worldwide mostly in Asia, Europe and South America. According to IBM, only 6 percent of North American computers have been infected.
While today may be a non-event, Conficker could be used to create harm in the future. Possiblities include a massive botnet, which would give Conficker's authors control over millions of computers worldwide. The botnet could then be used to attack corporate or government networks, commit identity theft, or deliver massive amounts of spam. Security experts warn that all Windows users must make sure their operating system and antivirus programs are up to date with the latest patches and virus protections. So far, Windows is the only operating system known to be vulnerable to Conficker.
(PCW)